Cybersecurity is one of the most critical and challenging undertakings for modern enterprises. If a company employs a robust suite of preventative tools and manages to avoid any breaches, it is still spending a lot of money in an area that doesn’t deliver a noticeable, direct benefit to stakeholders (as compared to lowering prices, paying employees more, or raising the dividend). But if a company’s systems are hacked, its operations could be disrupted, its customers may lose trust in the business, and it may be financially liable for legal and regulatory issues. Cyber breaches can be an existential risk.
Unfortunately, there is no standard playbook for cyber defense and success is never guaranteed. Even if a Chief Information Security Officer (CISO) has the best intentions and an unlimited budget there is no out-of-the-box, one-size-fits-all solution that they can buy. Every organization has unique requirements and challenges depending on the nature of their business and existing IT architecture. Additionally, even the best tools are still vulnerable to attacks enabled by human behavior; whether someone falls victim to a sophisticated social attack or is an intentional saboteur, it doesn't really matter.
Security is also not just a single function or tool but something that touches multiple parts of an organization. And successful defense requires not just the IT department but the buy-in and support of all senior leaders and business units. Thus, it is no surprise that cyber defense has become exceedingly complicated and is constantly evolving.
This makes cybersecurity stocks one of the most dynamic opportunities for active managers. A review of the biggest trends in cybersecurity brings the scope of the opportunity as well as the challenges of navigating the perpetually shifting landscape into focus.
It is worth reviewing some of the original cybersecurity tools available, both to understand why they are no longer sufficient as well as to give a better appreciation of the progress made. Simplistically, it all began with antivirus software. Software would periodically scan a system for known malicious code or suspicious behavior. If a threat was found it could be quarantined and deleted. The key point is that these tools only worked to find things that had already been seen before and were included in their threat libraries. Thus, they were vulnerable to things that hadn’t been seen before, so-called “zero day threats.” But they were also at risk if users did not habitually update to the latest version. As such, ambitious cyber criminals were easily able to stay ahead of antivirus programs.
Firewalls were the other key tool in early cybersecurity. Originally standalone appliances, they were deployed at the perimeter of a network to identify and block attacks. They act largely like a moat around a castle – if threats are kept outside the castle walls then the citizens will be safe inside (within the network). While firewalls have significantly evolved in terms of sophistication and capability, they aren’t much help if a threat does manage to breach the network. The rise of mobile devices, cloud computing, and remote work made securing the network perimeter that much more challenging. In some sense, the “network edge” dissolved.
The vulnerabilities in traditional cybersecurity tools and evolving networking landscape led to the rise of “zero trust” security. While this doesn’t imply the abandonment of perimeter security, a zero trust security framework essentially recognizes that breaches can and will happen. But when they do, the damage can be limited if a given user can only access the systems and data that they are authorized to, rather than move unencumbered across everything on the network.
The adoption of zero trust architectures intersected with the rise of a variety of specific point solutions designed to manage network access, defend a growing number of attack surfaces, and mitigate damage after a threat was identified.
Exhibit 1 below describes some of the tools that CISOs are deploying to ensure they have robust, end-to-end protection. Besides the large number of tools needed, relying too much on any one vendor could be a risk as well as the security vendor’s own tools could fail (or the vendor itself could even be hacked).
Exhibit 1: Examples of Modern Cybersecurity Tools

Source: Driehaus Capital Management LLC
Moreover, corporate directors and officers can be in breach of their fiduciary duty and even be held personally liable for cybersecurity breaches. Unsurprisingly, industry surveys show cybersecurity is the area of IT spending that is least likely to get cut and instead will continue to grow, even in the current challenging macro environment. When in doubt, buy another product!
This is how it came to be that some large enterprises employ upwards of fifty separate security products. The time and skill to effectively manage this multi-layered approach is challenging even for the most sophisticated customers. But the pendulum seems to be starting to swing back the other way.
A desire to consolidate vendors has emerged as buyers are increasingly trying to simplify their cybersecurity systems and optimize their budgets. CISOs are also increasingly aware that even if they buy every best-of-breed point solution available, there can still be gaps between the tools if they are not well integrated. A report by IBM showed that organizations using more than 50 security tools ranked themselves lower in their ability to detect and respond to attacks.1 Enterprises are starting to realize that buying from five to ten leading vendors can offer a simpler, more integrated, and ultimately more effective solution (less than this may expose an organization to unacceptable risk from the security vendor itself being compromised or negligent).
Networking, which is highly related to cybersecurity, is also seeing meaningful changes to support modern work requirements. Historically, many corporates were set up with an on-premise datacenter and network at their headquarters. Satellite or “branch” offices would then access enterprise applications and data via a physical networking infrastructure known as Multiprotocol Label Switching (MPLS) – essentially a dedicated hardware connection that routes traffic along predetermined network paths. While MPLS has proven to be a secure way to access a network, it has struggled to keep pace with enterprises’ modern IT needs.
The primary reason for this is the increased use of cloud services. Essentially, any user that wants to use a cloud application would have to route their request through MPLS to the enterprise headquarters and then have it routed to the cloud supplier, as opposed to connecting directly with the cloud service. With the increased use of cloud services and employees more geographically spread out due to hybrid working, relying on MPLS has become increasingly inefficient, slow, and costly.
The emerging answer to these challenges is Software-Defined Wide Area Network (SD-WAN) technology, which started to see initial adoption around 2017. This networking architecture extends networks over large geographical distances. The key benefits of SD-WAN include: software that automatically choose the best path to route data packets, more flexibility, and the ability to centrally monitor network performance and traffic. With SD-WAN there is no need for all traffic to flow through the headquarter’s datacenter. The practical takeaway is that it makes for a better experience for both users and network administrators.
Exhibit 2: SD-WAN
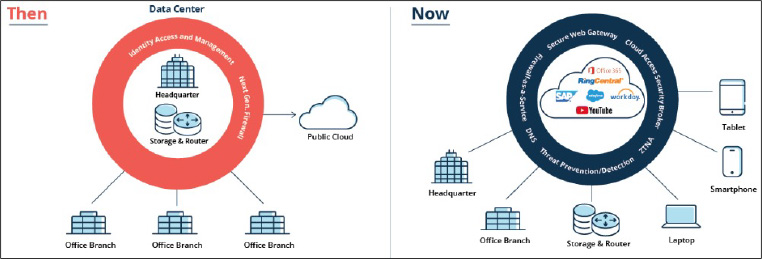
Source: Aruba Networks
Of course, cybersecurity is a paramount concern when changing your network configuration to SD-WAN. Fortunately, SD-WAN enables the ability to directly integrate security with networking (as opposed to having cyber security as an overlay on top of your network). Gartner coined the term Secure Access Service Edge (SASE) in 2019 to describe this convergence. SASE is the idea of consolidating multiple networking and security functions into a single integrated service.
Exhibit 3: Advantages of SASE
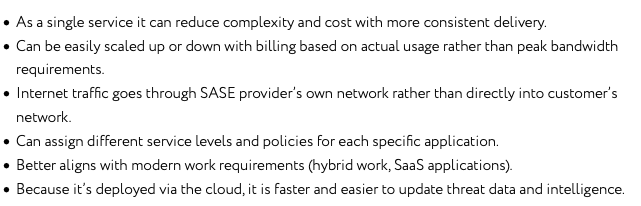
Source: Driehaus Capital Management LLC
Today, SASE is more a vision of the future and a model to strive for than a practical reality. Many enterprises will continue to rely on a hybrid of MPLS, SD-WAN, on-premise security, and SASE. Moreover, while the vendors themselves are running hard to build out their SASE offerings, it may be some time before they are prepared to meet all the needs of a large enterprise (e.g. a vendor needs their own distributed network with points of presence across all regions to avoid latency issues).
In summary, given the risks of breaches and the evolving threat landscape, enterprises have adopted a wide variety of solutions to try to protect themselves. The shift to the cloud and changes in working behavior that arose during the pandemic have only made the task of securing applications, data, and access more challenging. Cybersecurity customers are increasingly looking to consolidate vendors and tools to simplify their systems. Changes in networking architecture offer the potential for a more flexible and integrated solution, although implementation challenges remain. Additionally, given the high-stakes and reluctance to move too fast before solutions are entirely ready, many enterprises will move incrementally, ensuring these will be measured transitions.
While cybersecurity has greatly evolved over the last two decades, the industry is more likely to see accelerated change from here rather than stagnation. For example, the recent explosion of generative AI could lead to novel, more sophisticated threats, while simultaneously lowering the time and resources required to create them. In turn, new tools will be required for defense. This back-and-forth between attackers and cyber defense has been the story of the industry since its inception. This unending change will continue to create opportunities and risks for customers, cybersecurity vendors, and investors alike.
1IBM Study: Security Response Planning on the Rise, But Containing Attacks Remains an Issue - Jun 30, 2020
This information is not intended to provide investment advice. Nothing herein should be construed as a solicitation, recommendation or an offer to buy, sell or hold any securities, market sectors, other investments or to adopt any investment strategy or strategies. You should assess your own investment needs based on your individual financial circumstances and investment objectives. This material is not intended to be relied upon as a forecast or research. The opinions expressed are those of Driehaus Capital Management LLC (“Driehaus”) as of May 2023 and are subject to change at any time due to changes in market or economic conditions. The information has not been updated since May 2023 and may not reflect recent market activity. The information and opinions contained in this material are derived from proprietary and non-proprietary sources deemed by Driehaus to be reliable and are not necessarily all inclusive. Driehaus does not guarantee the accuracy or completeness of this information. There is no guarantee that any forecasts made will come to pass. Reliance upon information in this material is at the sole discretion of the reader.
Other Commentaries
Driehaus Global Equity Strategy December 2023 Commentary with Attribution
By Thomas Ansen-Wilson, CFA
Driehaus Global Equity Strategy September 2023 Commentary with Attribution
By Daniel Burr, CFA